Note: This is the third of three blog entries from Online Tech Director of Infrastructure Nick Lumsden reflecting on his key takeaways from EMC World 2014: 1. Speed of Change, 2. Shift in Ownership of IT Dollars, 3. Transition to IT-as-a-Service.
IT-as-a-Service: Need for speed and drive to align is changing operating model
Posted on July 31, 2014 by April Sage
Posted in General IT
Shift in ownership of IT dollars: Competition makes everyone better
Posted on July 31, 2014 by April Sage
Note: This is the second of three blog entries from Online Tech Director of Infrastructure Nick Lumsden reflecting on his key takeaways from EMC World 2014: 1. Speed of Change, 2. Shift in Ownership of IT Dollars, 3. Transition to IT-as-a-Service.
Posted in General IT
Speed of change: Enterprise business technology advancing daily (and faster!)
Posted on July 31, 2014 by April Sage
Note: This is the first of three blog entries from Online Tech Director of Infrastructure Nick Lumsden's reflecting from EMC World 2014: 1. Speed of Change, 2. Shift in Ownership of IT Dollars, 3. Transition to IT-as-a-Service.
Posted in General IT
After deep dives into the world of encryption as it relates to privacy, security and compliance and how it functions at thesoftware level, Online Tech’s “Tuesday at 2” webinar series concluded its three-part encryption presentation with a look at encryption at the hardware and storage levels.
Steve Aiello led the conversation and handled aspects of encryption for Microsoft-driven hardware and guest co-host Mark Stanislav took over for the Linux-focused stretch of the presentation. Both explored the variety of places encryption can be employed to mitigate risk of data loss or breach, and some of the considerations for choosing the most appropriate method to employ.
Posted in Cybersecurity
The ‘What, Why, How and Who’ of Data Encryption for HIPAA Compliance
Posted on July 31, 2014 by April Sage
Before law school, Brian Balow studied journalism for five semesters of his undergraduate years, so using an adaptation of the reporting axiom ‘who, what, where, when, why and how’ was a logical way to break down the points in his webinar, Removing the ‘Cryptic’ from ‘Encryption’ – HIPAA and the Meaning of Secure PHI.
And because the former cum laude graduate of the University of Georgia School of Law is now a leading attorney concentrating his practice at Dickinson Wright PLLC in the areas of information technology – and a valued contributor to Online Tech’s series of educational webinars – his arbitrary arrangement of that axiom was deemed admissible by the court of public opinion.
Here is what you can expect to learn by viewing a replay of the 51-minute presentation about Protected Health Information (PHI) and data encryption as it relates to HIPAA and Meaningful Use compliance:
- What (requires protection)?
- Why (is protection important)?
- How (should it be protected)?
- Who (should encrypt)?
That’s a lot of questions that need to be answered, something Balow noted when he was ‘doing a little historical digging’ into the legislative history and language around HIPAA in preparation for the webinar.
“It’s interesting and a little disappointing that when you look back even in 1996, there was a focus on the electronic exchange of health information. They knew this was the wave of the future even back then,” Balow said. “Fast forward to September of 2013 and we’re still talking about issues that pertain to electronic health records, and how they’re protected, and Meaningful Use to try to incentivize organizations and providers to adopt records. So we’re coming up on 20 years and we’re still working on this stuff.”
A summarized recap of the presentation follows.
What (requires protection)?
Protected Health Information (PHI) must be protected. Balow covered the long, legalese definition, but said it comes down to this: Any electronic health information that identifies an individual or can be used to identify an individual must be encrypted.
Balow notes that there is a lot of overlap between HIPAA, Meaningful Use and other personally identifiable information (PII)-centered laws such as state data breach notification laws, the PCI Data Security Standard, the Gramm-Leach-Bliley Act, etc. “The point being,” Balow said, “If it’s individually identifiable information in the healthcare industry, it’s likely PII in other industries, as well.”
Why (is protection important)?
Balow covered the HIPAA Enforcement Rule, Security Rule and Breach Notification Rule in depth. He notes the security rule “is the part of HIPAA that really has caused most of the noise over the last nine months since the final rule came out, because there was a host of business associates out there who suddenly were directly liable … who did not have the administrative, technical and/or physical safeguards in place that were required of them.”
Cited in the webinar is Office for Civil Rights statistics that show 9,411 investigations resolved in 2012, a number Balow says is an increase from zero not many years ago. He also covers HIPAA civil money penalties resulting from failure to encrypt.
Balow points out that one reason to encrypt data is because the Breach Notification Rule requires notification of a breach only after unsecured protected health information. Electronic PHI becomes secured through the adoption of encryption techniques approved by HIPAA regulations.
“Putting aside the potential civil money penalties – which are not insignificant – if you are dealing with unsecured PHI and have a breach, you have the added cost of hiring a lawyer or using internal resources to do an analysis and prepare the notices and figure out everyone you have to track down. Keep in mind you’ll probably have to do that with state data breach notification laws and potential federal trade commission issues related to your privacy policy. As well as the bad publicity that goes with it. If I encrypt, I need not worry about this.”
Balow also describes how the use of encryption to reach Meaningful Use, Stage 2 status is more focused on end-user device encryption, such as laptops, flash drives and mobile hardware.
How (should it be protected)?
For HIPAA compliance, encryption is the use of an algorithmic process to transform data into a form in which there is a low probability of assigning meaning without use of a confidential process or key and that process or key must be stored separate from the data. Any process must be judged to meet National Institute of Standards and Technology (NIST) standards.
Noting he’s an attorney and not a technology expert, Balow pointed to an Online Tech resource to help answer this question: http://resource.onlinetech.com/encrypting-data-to-meet-hipaa-compliance
The Centers for Medicare & Medicaid Services, who deem Meaningful Use status, also emphasize the importance of organizations ‘including in its security risk analysis an assessment of the reasonable and appropriateness of encrypting electronic protected health information as a means of securing it, and where it is not reasonable and appropriate, the adoption of an equivalent alternative measure.’
Translation, counselor?
“I think what they’re really saying is, if you are properly performing a HIPAA security risk analysis – which you are required to do if you are a covered entity or a business associate – then whatever conclusion you reach as it pertains to encryption under that regime should suffice under the meaningful use regime,” Balow said.
Balow also took a moment to suggest finding additional information on the U.S. Department of Health and Human Services and the Centers for Medicare and Medicaid Services websites.
“They’ve done a lot of work, gone through a lot of effort, to put resources and information on their websites to help people in the industry to understand and comply with what is now required under HIPAA and with respect to the Meaningful Use regulations,” Balow said.
Who (should encrypt)?
Balow said he has been guilty in the past of making broader statements in certain contexts as it relates to ‘who should encrypt?’ than really are appropriate. “It’s an easy conclusion to reach, why wouldn’t we encrypt?” Balow said. “But it is not necessarily a one size fits all. Context does matter.”
He notes encryption is one of many tools to protect data, and is not required in all environments. A ‘wild example:’ A doctor in the Upper Peninsula of Michigan who only takes cash and has all paper records doesn’t need to encrypt.
Beyond that, and some other less unusual examples, Balow said that if you are an Eligible Professional (EP), Eligible Hospital (EH) or Critical Access Hospital (CAH), the likelihood is that encryption makes sense to achieve Meaningful Use status.
“The way that I read the regulations is that if you want to meet Stage 2, you are going to encrypt,” Balow said. “It would probably be a rare case where you could get out of Stage 2.”
Even those organizations that don’t take Medicare and Medicaid – and therefore aren’t interested in Meaningful Use compliance – still need to make a serious risk assessment, he said. He noted the previously-mentioned Breach Notification Rule alone may be enough to drive a decision to encrypt.
“You are still subject to HIPAA as a covered entity or a business associate. You don’t care about Meaningful Use, but you still need to do that Security Rule risk assessment that will guide your decision on whether to encrypt,” he said. “Remembering it’s an addressable standard and you have to prove why you shouldn’t encrypt – why your technical safeguards, physical safeguards and administrative safeguards are sufficient so additional steps are not required.”
Posted in Cybersecurity
"What took so long?"
Posted in Cybersecurity
Posted in Cybersecurity
HIPAA Glossary of terms
Posted on July 31, 2014 by April Sage
It's a jungle out there in healthcare, and we want to make sure you have the info you need to cut through some of the jargon. Here's a comprehensive glossary of basic HIPAA terms to define the key phrases you need to understand HIPAA compliance today.
Business Associates
Anyone who has access to patient information, whether directly, indirectly, physically or virtually. Additionally, any organization that provides support in the treatment, payment or operations is considered a business associate, i.e. an IT company or a billing and claims processing company. Other examples include a document destruction company, a telephone service provider, accountant or lawyer. The business associates also have the responsibility to achieve and maintain HIPAA compliance in terms of all of the internal, administrative and technical safeguards. A business associate does not work under the covered entity’s workforce, but instead performs some type of service on their behalf.
Business Associate Agreement
The agreement standard document that clearly defines the roles and responsibilities of a business associate and the covered entity. The other key piece of the Business Associates Agreement is the assurance that businesses will take proper steps to implement the appropriate administrative, physical and technical safeguards.
Covered Entities (CE)
Anyone who provides treatment, payment and operations in healthcare. It could include a doctor’s office, dental office, clinics, psychologist, nursing home, pharmacy, hospital or home healthcare agency. This also includes health plans, health insurance companies, HMOs, company health plans and government programs that pay for health care. Health clearing houses are also considered covered entities.
Electronic Data Interchange (EDI)
The communication or exchange of business documents between companies via computer.
Electronic Health Records (EHR)
Electronic health records are any electronic record of patient health information generated within a clinical institution or environment, such as a hospital or doctor’s office. This may include medical history, laboratory results, immunizations, demographics, etc.
Electronic Protected Health Information (EPHI)
All individually identifiable health information that is created, maintained or transmitted electronically.
Healthcare Clearinghouse
An organization that standardizes health information. One example is a billing company that processes data from its initial format into a standardized billing format.
Health Information
Patient information collected by a health plan, health care provider, public health authority, employer, healthcare clearinghouse or other organization that falls under covered entity.
Healthcare Insurance Portability and Accountability Act (HIPAA)
Developed in 1996, the acronym HIPAA stands for Healthcare Insurance Portability and Accountability Act. Initially created to help the public with insurance portability, they eventually built administrative simplifications that involved electronic, medical record technology and other components. In addition, they built a series of privacy tools to protect healthcare data.
Health Information Technology for Economic and Clinical Health (HITECH)
In 2009, as part of the American Recovery and Reinvestment Act (ARRA), there was an act within that called HITECH, short for The Health Information Technology for Economic and Clinical Health Act. The act included incentives offered to physicians in private practices, as well as institutional practices to implement and adopt electronic medical records.
In addition to incentives, the act included a series of fines to help enforce HIPAA rules. HITECH also mandated that business associates of covered entities, as well as the covered entities themselves, were responsible for the same level of HIPAA compliance.
HIPAA Audit
A HIPAA audit is based off a set of regulations, standards and implementation specifications. The audit is an analysis that helps to pinpoint the organization’s current state and what steps need to be taken to get the organization compliant.
An evaluation is part of the audit - a company must perform an evaluation and undergo periodic evaluations once a year at minimum. As technology changes, different components are added to an organization’s infrastructure and they should be re-evaluated.
While covered entities need to undergo HIPAA audits, third-party business associates also need to comply. This includes any company that might provide services for a covered entity, for example, an application hosted in a cloud and provided to a covered entity.
HIPAA Violations
If a company fails to comply with HIPAA rules, they are subject to both civil and criminal penalties.
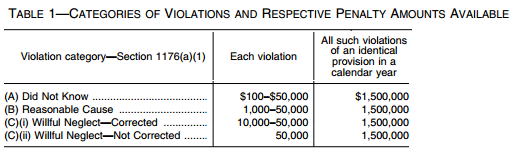
Civil Penalties
Established by the American Recovery and Reinvestment Act of 2009 (ARRA), the tiered civil penalty structure below determines the cause and consequences of the HIPAA breaches. The Secretary of the Department of Health and Human Services has the ability to ultimately determine fines and penalties due to the extent of the violation on a case-by-case basis.
Due Diligence
An organization is in violation, but they have taken every possible step they could have foreseen to prevent that.
Minimum fine: $100 per incident with annual maximum of $25,000 for repeat violations
Maximum fine: $50,000 per violation with annual maximum of $1.5 million for repeat violations
Reasonable Cause
The steps have been taken, but something was not addressed. For example, a company went into a HIPAA audit and provided a gap analysis, but something wasn’t addressed yet. The violation is due to reasonable cause and not willful neglect.
Minimum fine: $1,000 per incident with annual maximum of $100,000 for repeat violations
Maximum fine: $50,000 per incident with annual maximum of $1.5 million for repeat violations
Willful Neglect
There are two types of willful neglect. The first is when a company clearly ignores the HIPAA law but corrects their mistake within the given amount of time.
Minimum fine: $10,000 per incident with annual maximum of $1.5 million for repeat violations
Maximum fine: $50,000 per violation with annual maximum of $1.5 million for repeat violations
The second type of willful neglect is when a company ignores the HIPAA law and does not correct their mistake.
Minimum fine: $50,000 per incident with annual maximum of $1.5 million for repeat violations
Maximum fine: $50,000 per incident with annual maximum of $1.5 million for repeat violations
Criminal Penalties
The U.S. Department of Justice established who can be held liable for HIPAA violations due to criminal activity. This includes covered entities and any specified individual working under a covered entity. Anyone who knowingly misuses health information can be fined up to $50,000 including up to a year of imprisonment. More serious offenses call for higher fines and prison time.
Individually Identifiable Health Information
A subset of health information, this includes demographic information about an individual’s health that identifies or can be used to identify the individual. This includes name, address, date of birth, etc.
OCR HIPAA Audit Protocol
Up through early 2012, there was no federal standard for third-party auditors to conduct a HIPAA audit. With the publication of the new Office for Civil Rights audit protocol, auditors are able to gain a more consistent direction on how the OCR will conduct HIPAA audits in the future. The new protocol covers requirements found in the HIPAA Security Rule, Privacy Rule and Breach Notification Rule. Read more here.
Privacy Rule
The part of the HIPAA rule that addresses the saving, accessing and sharing of medical and personal information of an individual, including a patient’s own right to access.
Protected Health Information (PHI)
This includes any individually identifiable health information collected from an individual by a healthcare provider, employer or plan that includes name, social security number, phone number, medical history, current medical condition, test results and more.
Security Rule
The part of the HIPAA rule that outlines national security standards intended to protect health data created, received, maintained or transmitted electronically.
Resources:
Posted in HIPAA
There’s a fundamental change underway in the healthcare system, which is shifting away from a traditional fee-for-service model toward a more accountable, patient-centered model of care.
Accountable care organizations (ACO) are popping up across the country with what’s being referred to as a Triple Aim: better care for individuals, better health for populations, and lower per capita costs.
In a recent Online Tech Tuesdays at Two webinar session, attorneys Tatiana Melnik and Carrie Nixon extensively defined and discussed the ACO model (what is it, why we are moving in that direction, where the patient fits into the model, and some early success stories), the role technology plays in its emergence, and ways to minimize and mitigate legal risks in the framework.
Melnik specializes in IT legal issues with a specific emphasis on healthcare, privacy, and security. Nixon is president of Accountable Care Law & Policy and a founding member of Healthcare Solutions Connection, a network of expert consultants providing solutions for the healthcare industry.
“We’re moving to the ACO model because really, the current system is unsustainable,” said Melnik “Baby Boomers are aging and are straining a system that is already having a difficult time managing and sustaining a patient population.”
Titled PHI in the ACO – Risk Management, Mitigation and Data Collection Issues, the hour-long webinar covered multiple must-know topics for healthcare and health IT personnel – whether they’re already part of an ACO, plan to be part of an ACO, or are simply interested in the movement.
Melnik and Nixon dove into several technology issues in their first session. Some highlights:
“Data collection and analytics are really the keys to success in the ACO environment,” Melnik said. “This is because quality metrics must be collected and reported to (Centers for Medicare and Medicaid Services) and must also be shared among the ACO participants so that they can provide better care to the beneficiaries.”
Nixon said one of her key messages during the session was to “underscore the importance of data, data, data. Have your data collection mechanisms in place, and look at your data. Look at your data. Analyze your data. Think about what it means. Think about ways that you can improve.”
However, all the record-keeping requirements of an ACO are extensive – records must be kept for a minimum of 10 years, plus six more if there’s a termination, dispute or allegation of fraud against an ACO. Melnik noted that keeping information for 16 years or longer requires a heavy investment for data storage and data retrieval costs.
Paraphrasing Melnik: Data sharing and collection requires an advanced IT infrastructure, which means ACOs have to understand how the IT environment works and how the data migrates through the system. At the same time, people and processes must be in place so data is understood. Analytics are useless nobody in the system can explain what the numbers mean and how to improve on the information that you’re getting.
Nixon mentioned an ACO that hired three employees who deal strictly with data.
“How many ACOs are considering that they have to do that? Or, are they thinking, ‘We’ll figure that out when we get to that point’?” Melnik said. “That’s really problematic, because that can impact the long-term success of your project. You need to have those considerations in place at the forefront and really account for those costs at the beginning.”
The co-hosts also discussed the need for interoperability, considering the integration of personal health records, mobile devices and other technology with electronic health records (EHR). When a large number of providers with their own EHR systems merge and want to use personal health records (to meet Meaningful Use standards) and mobile device integration (to improve patient engagement), technology issues expand exponentially.
Melnik noted the Federal Trade Commission is involved in assessing whether some software vendors are improperly exerting control on competition when it comes to interoperability. She suggested reviewing materials from the FTC’s Examining Healthcare Competition workshop held in March.
Melnik also discussed how the need for data breach insurance (and the amount of data breach insurance) must be carefully evaluated when forming an ACO. “Consider the recently released report from the Ponemon Institute finding that the cost to remediate a breach in the healthcare space is $359 per record, compared to a $201 dollar industry average,” Nixon said. “If you have 50,000 records involved in a breach, that’s $17.9 million. How many organizations have those kinds of funds to pay out that amount?
If your organization involved with or supporting an Accountable Care Organization? Let us know what questions you are facing.